
How does the Azure Firewall relate to Network Security Groups (NSG)? NSG and Azure Firewall are complementary providing better in-depth network security. An NSG provides distributed network layer traffic filtering to limit traffic to resources within virtual networks. Azure Firewall is a fully stateful centralized network firewall as-a-service, providing network and application level protection across virtual networks.
This public preview supports the following features
- Outbound FQDN filtering
- Network traffic filtering rules
- Outbound SNAT support
- Azure Monitor logging
Time to put this Preview Release to the test! In this blog post I’m test-driving Azure Firewall Preview by testing a specific Use Case, to secure outbound traffic from a Remote Desktop Services environment. This blog post describes how to leverage Azure Firewall to secure Remote Desktop Services sessions running on Azure. The setup in this blog post based on RDS on Azure IaaS but is also applicable to the upcoming Remote Desktop modern infrastructure (RDmi). In fact, the deployment is exactly the same since both RDS on IaaS as well as RDmi use RD Session Hosts running in your Azure Subscription based on IaaS.
The first step is to enable your Azure Subscription to use the Public Preview of Azure Firewall.
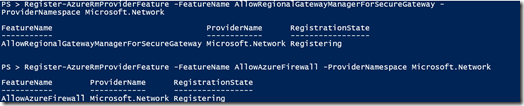
Logon to Azure RM using PowerShell and run the following two commands:
Register-AzureRmProviderFeature -FeatureName AllowRegionalGatewayManagerForSecureGateway -ProviderNamespace Microsoft.Network
Register-AzureRmProviderFeature -FeatureName AllowAzureFirewall -ProviderNamespace Microsoft.Network
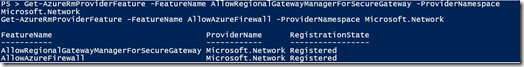
The registration can take ~30 minutes to complete, but in my case, it took ~10 minutes. You can check the status of the registration by running these two commands. Once completed it should state registered.
Get-AzureRmProviderFeature -FeatureName AllowRegionalGatewayManagerForSecureGateway -ProviderNamespace Microsoft.Network
Get-AzureRmProviderFeature -FeatureName AllowAzureFirewall -ProviderNamespace Microsoft.Network
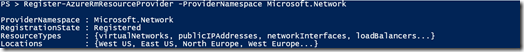
Once the status shows registered, run the following command to finish the registration
Register-AzureRmResourceProvider -ProviderNamespace Microsoft.Network
Before we can create the Azure Firewall, a new subnet must be created. For the purpose of this lab environment I’m creating a new subnet within my existing Vnet where a separate subnet with my RDS deployment already resides. For production deployments, a hub and spoke model is recommended, where the firewall is in its own VNet, and workload servers are in peered VNets.
The screenshot below shows the creation of the Subnet for the Azure Firewall. Note that the subnet name must be names AzureFirewallSubnet otherwise you will not be able to deploy the Azure Firewall.
Next, we can go ahead and create the Azure Firewall, which is available from the Azure Marketplace.
We need to specify the parameters. Make sure you select the existing Vnet where as part of a previous step, the subnet called AzureFirewallSubnet was created. Also, I noticed that the Azure Firewall needs to be created in the same ResourceGroup as the existing Vnet.
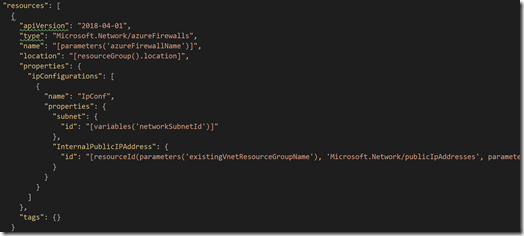
You can of course also use a JSON template to create the Azure Firewall. Below is code snippet of how to create the Azure Firewall using JSON.
After the creation of the firewall, we need to create a new route table to make sure outbound traffic from the Subnet will go through the Azure Firewall.
Next, we associate the Route Table to subnet where our destination servers are located. In this example I selected the Subnet where the RD Session Host servers are running.
And finally, we need to add the route. For this example, we set the prefix to 0.0.0.0/24 and point it to the private IP-address of the Azure Firewall. This basically means that all outgoing traffic will flow through the Azure Firewall. Note that although the Azure Firewall is more of a managed service, we need to select virtual appliance here.
Now that the Azure Firewall and Route are in place, we can start defining rules in the firewall. For this use case we want to control traffic from the RD Session Host to the internet. For this example let’s say we are publishing a browser as a RemoteApp on RDS and want to control, basically whitelist, the URL’s the user can browse to, ultimately creating a “secure browser”.
In order to do so, we create the rule below. This basically says, anything from within the Subnet that we want to control is allowed http and https access to *github.com. Anything else will be rejected.
In this environment the RD Session Host server is a member of an Active Directory domain, where the Domain Servers are within a subnet within the same vnet. In scenarios where you are using an external DNS service, you also need to create a rule to allow DNS services. This can be done using a Network. Rule, the screenshot below shows an example of what that could look like.
And that’s it. We have just created a basic secure browser environment. Let’s logon to RDS as an end user and take a look at some of the results.
In this scenario, the RD Session Host server that is part of an RDS on Azure IaaS deployment is located on the Subnet with the Route and thus the Firewall in place.
We log on to Remote Desktop Services web client (HTML5) (which recently went to Preview 0.9.0 release)
And we open the Github published application.
We now running a secure browser with github.com from within a locally running chrome. Isn’t that what you’ve always wanted to do? Run IE inside Chrome? :) This is just an example of course, we could have also used mstsc or RD Web Access as well.
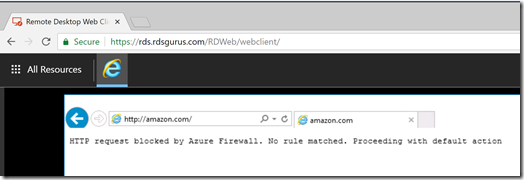
But anyway, let’s put the Azure Firewall to the test and browse to a different URL, amazon.com. We can now see the Azure Firewall at work, blocking that traffic based on the rules we defined.
This completed my first test. Obviously, this is just the first preview release of the Azure Firewall and we’ve only looked at a specific feature (Outbound FQDN filtering) to get some hands-on experience. It is however great to see Azure Networking evolving, and I’m looking forward to future features!

![clip_image002[5] clip_image002[5]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgypzfYEvXM6kiEAK58vNf_cvY0UnscQy6rrd7ngyzTP52bTuN1fRCKI28oAGmKtEiG9B4HUT7g0HgIPsrV-2-CLJ8ak74uIkFrEzCN_8BRobxW6-_NefS0L_seHBlLQ8Uw86cnPUflM-W-/?imgmax=800)
![clip_image004[4] clip_image004[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEifN4EConJVcjiXehN_KE_-FOxsUKOIemU8WmH3m8RkmlJ3e5E2wOLhT8zGeqBP65X69KqON1ieX10uhn_a8QUawKHTMhwo8Tv-Sybk1_-cJe_TvKDGFEaQAg1jHhqDGn5RjsR5ApNvqHsa/?imgmax=800)
![clip_image006[4] clip_image006[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEg0IzrzP6iG9KnfH8ZzvMGXDSuolTcZy90_wqXma1C868pm8_XNYC9KTM6vwR_4QqsUq923SlIaRK74dnBPZEGjrJp8lYVJ17WgFvzmNdXRjaoXMCe9_8Bqz56MipS1o1JD8txhqn869ExV/?imgmax=800)
![clip_image008[4] clip_image008[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjqlCSxGMT0jHEWb6mzkaqAl21qLHary8zAaqBF5GDVfg_FNhGKADJC2Rq9p80wWX6rUedbgA4jnUbuOwCFD568lCVnqavh0I9br_BwJgutiEE6wPMP-_tgsU_gBMtZACH-6LWB18UZfZVW/?imgmax=800)
![clip_image010[4] clip_image010[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjX6Hd4Nm-FaN3stjawCkD4qeFFPk6NfS0-cec8b63JY2Egr5Wncf9J8E4ZoLmk95QgXDeTLnhIAEf-KOzICScVfPPsl0Uyjlrz7PdEuMtORTNKoCW71QhxiCJo3QxhTBYzjit5pJlxTvdl/?imgmax=800)
![clip_image012[4] clip_image012[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhFun2O1YoZ9yhMgjBhgzZsGHbgBvelkuyvSLz29N3MCyFI7qU80MC4AvtMqKDDO-H8E6ZDAezMxIwi7UtY1jb31LCzMP1mtbs8Ha-RBJaVGpuOvhP-kCx16sqNRVB3NpRF-0ABsuyTdsIv/?imgmax=800)
![clip_image014[4] clip_image014[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiF96QDtiv3NZaHmfVcDHhBih7n6oxZZf7PFglSTH9TLyvDoSE3k8nY-zEFcnJADvmc6FMIVkfH9OPCcrCEVIqiENsYWx4sFiWwZb_Dz_AGmVqXsuClYW-VJKC_mATDYtGF0aiOB0E8c22v/?imgmax=800)
![clip_image016[4] clip_image016[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhguBaUFvplFXUsbmmYkU0859hWs5h18OV5m2KQsQJEGyRspEqPRysN28n-WRFqCs3PCEss6j_JvXZV_3LbC6wSvvDThxE_w5L5TEC6MoUox7FqbQV4blUMsjWMpIDGC_OSPIw7B1v9Tmx0/?imgmax=800)
![clip_image018[4] clip_image018[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEht-gQIUGoiC5HB0msoz7yrYQ4IhMhVtUe3Ac25rfEHcblX_zs-Zgoyt2vbO4tFJJ5DTw5y4HV1ovCPKm5zg0BHmx5xjxQ53_YEh4fpxIgtf_ENCwgr4yfxDxYK_T3-2HNlWxBfy6QlaPBv/?imgmax=800)
![clip_image020[4] clip_image020[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEibSIWqCkjF_xjw0w1PEGIHrE-kDu17u0p1wv91M0UI8v_ltKd-6gY7ZbxMqKI4oCfwU3j3soOOcf3uN4UKR1gnnMPKMZGhp4Gewl4U9TplLntw1TUgDrMQGuYwX4PYw37KUlqL-1vTl48N/?imgmax=800)
![clip_image022[4] clip_image022[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjv3cuih_gxcoV5k5aQ8wD5jch2sz1jxiFk2tbEERnfHojgrUzM3kyxt7hiVNQzOEegz8FJ09HDWzXzUEFAa84hGo4CWrchmEO4SIrYKu9wDIYgV1ESUmbL6Lg7g37ulualK_LYdsGe6ChS/?imgmax=800)
No comments:
Post a Comment