By now, you most likely heard about Windows Virtual Desktop (WVD) as the evolution of RDmi and how Windows10 Multi-session is part of that evolution. If not, these announcements we’re all made public during Microsoft Ignite 2018 last month. I previously published a blog post on news that was shared in a post that is called Windows Virtual Desktop, RDS 2019 and Multi Session Windows 10, What a week and I covered a recap of the sessions I presented myself in Orlando called Presented 2 sessions at Microsoft Ignite 2018, Orlando.
I have been part of the RDmi private preview program since the early days, almost a year ago, and I’ve had the privileged to test the early WVD platform as well. In this blog post I want to focus on one of the benefits of WVD, the ability to use Windows10 Multi-session.
At Ignite 2018, Microsoft officially announced the Windows10 Multi-Session, the first official multi-user Windows 10 version that allowed multiple concurrent users to connect. This basically means that Windows10 can now also be used as an “RD Session Host server”, where this was previously only possible using a Windows Server operating system. So why is this interesting and how is this beneficial for publishing Applications and Desktops?
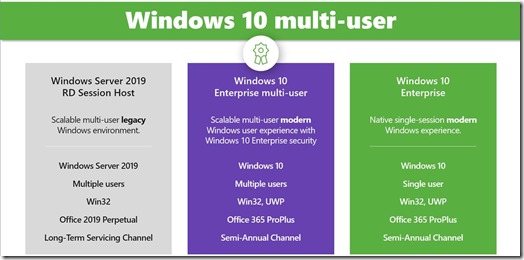
Let’s look at the three pillars in the below diagram (credits to various Microsoft Slide Decks used at Microsoft Ignite 2018).
- On the left-hand side, we have Windows Server RD Session Host. Traditionally, this has been widely used option to publish Applications and Desktops using RDS. The great thing about Windows Server RD Session Host is that it allows users to share available resources. Multiple users can connect to a server simultaneously making a very flexible, cost-effective and easy to manage solution. The obvious downside of this solutions is that it is based on Windows Server. This means that the user is presented with a different experience compared to his local modern Windows10. Modern Apps like for example Edge and Cortana are not available and it’s all based on a Long-Term Service Release.
- On the right-hand side we have Windows 10 in a Pooled or Personal VDI-like setup. Compared to Windows Server RD Session Host, this setup does allow the user to get the modern experience he is used to, including Universal Windows Apps. One of the downsides of this approach has always been that this is a one-to-one setup. Whether is a pooled or personal setup, every user runs his own Windows 10. This adds additional challenges in terms of scaling, complexity and in most scenarios resulted in less cost-effective setup. Over the years, many vendors have however been developing great suites and tools to remove parts of the complexity, add scaling and trim down the costs.
- In the middle Microsoft introduced Windows 10 Multi-Session, and this is basically best of both worlds. This approach has the multi-user benefits of RD Session Host and the modern experience benefits from Windows 10. What’s also important to note is that going forward, Windows 10 will be the only option to run Office 365 Pro Plus. Windows Server 2019 will only support Office 2019 Perpetual meaning you will miss out the all of the collaboration features.
With all of the improvements of RDS in Windows Server 2019, Microsoft is definitely not giving up on RD Session Host. But based on the all of the arguments outline above, I’d state that Windows 10 Multi-User is the RD Session Host of the future. There is one caveat worth mentioning, Windows 10 multi-user only comes with WVD meaning you cannot run this outside of Azure. For workloads that cannot move to Azure, Windows Server 2019 will be the way to go.
There are two questions I get very frequently when talking to people about WVD.
- Microsoft introduced RDmi last year, is WVD replacing RDmi?
The answer is no. WVD is evolved on RDmi and uses the RDmi platform rather than replacing it. This means that all of the good things of RDmi like Multi Tenancy and AAD support still exist. The main difference is that you will not be hosting the RDS infrastructure roles in your own subscription (the model that RDmi was) but instead Microsoft will host them for you.
- Does Windows Virtual Desktop only support publishing Full Desktops and not RemoteApps?
The answer is no again. Despite the name Windows Virtual Desktop, a Host Pool in WVD is very flexible and can publish Full Desktop and RemoteApps. It can even host a mix of Desktops and Remote Apps coming from servers and clients that go back as far back as Windows7 (with free extended support) and Windows Server 2012R2!
Windows Virtual Desktop can be provisioned using the Azure Marketplace and using ARM Templates. Below is a preview screenshot of the marketplace entry, note that this may be subject to change.
Once WVD is provisioned, management can be performed using PowerShell or Rest API.
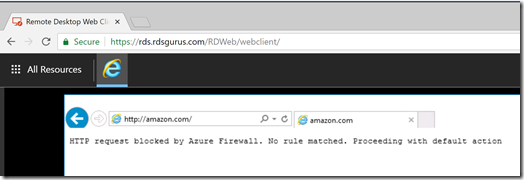
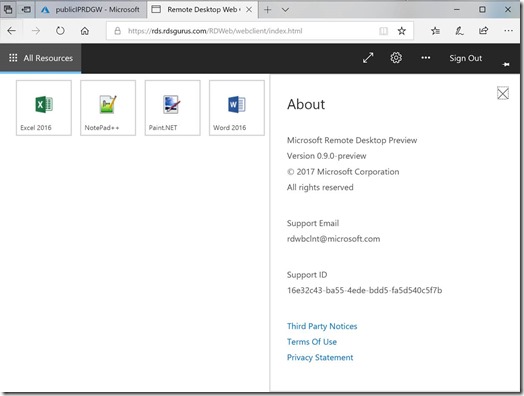
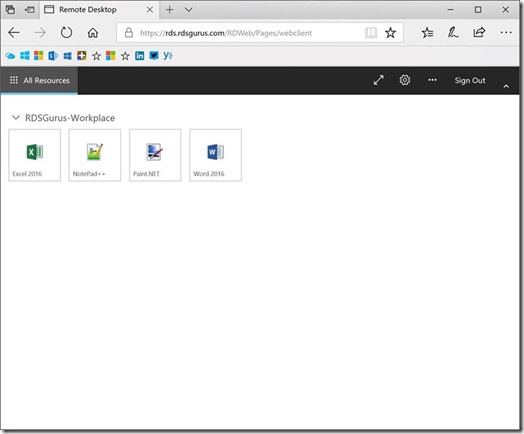
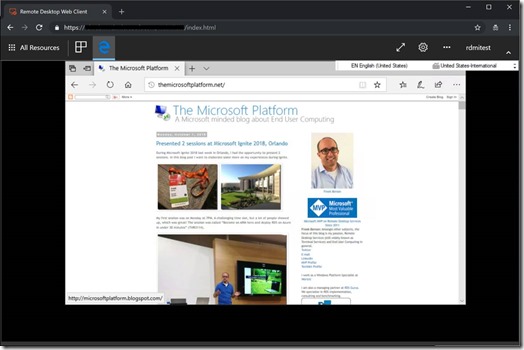
In the below screenshot you can see a mix of RemoteApps and Full Desktop within the HTML5 client of WVD. The RemoteApps as well the Full Desktop is based on Windows 10 Multi-Session.
And you can see even Edge (not available in a Windows Server RDSH) is now published here as a RemoteApp! And yes, that means I can run Microsoft Edge inside Chrome! :)
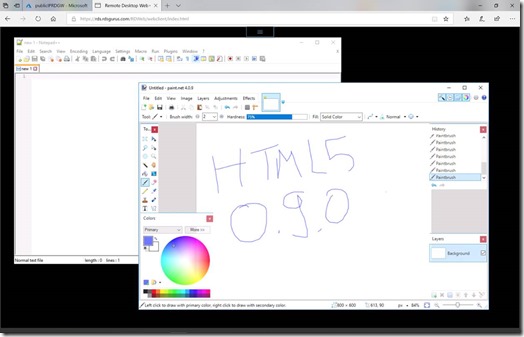
Besides HTML5, I can also leverage the RemoteApp & Desktops Connections applet and configure it with the WebFeed URL from WVD resulting, in the WVD Desktop & RemoteApps available in my local start menu!
Here is Edge Running as a RemoteApp using the full mstsc experience. You can tell it is a RemoteApp by looking at the taskbar where an RDP icon appears over the Edge icon.
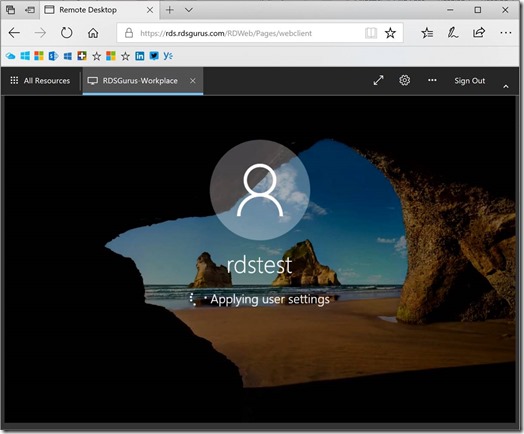
When opening Winver and Task Manager we get prove that this really is the multi-user version of Windows 10.
And for the 3rd most asked question:
- When will WVD become available?
WVD is planned to become Public Preview soon (later this year) and General Availability is expected early 2019. If you want to get a notification as soon as the Public Preview is available, sign up here: aka.ms/wvdpreview.


















![clip_image002[5] clip_image002[5]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgypzfYEvXM6kiEAK58vNf_cvY0UnscQy6rrd7ngyzTP52bTuN1fRCKI28oAGmKtEiG9B4HUT7g0HgIPsrV-2-CLJ8ak74uIkFrEzCN_8BRobxW6-_NefS0L_seHBlLQ8Uw86cnPUflM-W-/?imgmax=800)
![clip_image004[4] clip_image004[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEifN4EConJVcjiXehN_KE_-FOxsUKOIemU8WmH3m8RkmlJ3e5E2wOLhT8zGeqBP65X69KqON1ieX10uhn_a8QUawKHTMhwo8Tv-Sybk1_-cJe_TvKDGFEaQAg1jHhqDGn5RjsR5ApNvqHsa/?imgmax=800)
![clip_image006[4] clip_image006[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEg0IzrzP6iG9KnfH8ZzvMGXDSuolTcZy90_wqXma1C868pm8_XNYC9KTM6vwR_4QqsUq923SlIaRK74dnBPZEGjrJp8lYVJ17WgFvzmNdXRjaoXMCe9_8Bqz56MipS1o1JD8txhqn869ExV/?imgmax=800)
![clip_image008[4] clip_image008[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjqlCSxGMT0jHEWb6mzkaqAl21qLHary8zAaqBF5GDVfg_FNhGKADJC2Rq9p80wWX6rUedbgA4jnUbuOwCFD568lCVnqavh0I9br_BwJgutiEE6wPMP-_tgsU_gBMtZACH-6LWB18UZfZVW/?imgmax=800)
![clip_image010[4] clip_image010[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjX6Hd4Nm-FaN3stjawCkD4qeFFPk6NfS0-cec8b63JY2Egr5Wncf9J8E4ZoLmk95QgXDeTLnhIAEf-KOzICScVfPPsl0Uyjlrz7PdEuMtORTNKoCW71QhxiCJo3QxhTBYzjit5pJlxTvdl/?imgmax=800)
![clip_image012[4] clip_image012[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhFun2O1YoZ9yhMgjBhgzZsGHbgBvelkuyvSLz29N3MCyFI7qU80MC4AvtMqKDDO-H8E6ZDAezMxIwi7UtY1jb31LCzMP1mtbs8Ha-RBJaVGpuOvhP-kCx16sqNRVB3NpRF-0ABsuyTdsIv/?imgmax=800)
![clip_image014[4] clip_image014[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiF96QDtiv3NZaHmfVcDHhBih7n6oxZZf7PFglSTH9TLyvDoSE3k8nY-zEFcnJADvmc6FMIVkfH9OPCcrCEVIqiENsYWx4sFiWwZb_Dz_AGmVqXsuClYW-VJKC_mATDYtGF0aiOB0E8c22v/?imgmax=800)
![clip_image016[4] clip_image016[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhguBaUFvplFXUsbmmYkU0859hWs5h18OV5m2KQsQJEGyRspEqPRysN28n-WRFqCs3PCEss6j_JvXZV_3LbC6wSvvDThxE_w5L5TEC6MoUox7FqbQV4blUMsjWMpIDGC_OSPIw7B1v9Tmx0/?imgmax=800)
![clip_image018[4] clip_image018[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEht-gQIUGoiC5HB0msoz7yrYQ4IhMhVtUe3Ac25rfEHcblX_zs-Zgoyt2vbO4tFJJ5DTw5y4HV1ovCPKm5zg0BHmx5xjxQ53_YEh4fpxIgtf_ENCwgr4yfxDxYK_T3-2HNlWxBfy6QlaPBv/?imgmax=800)
![clip_image020[4] clip_image020[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEibSIWqCkjF_xjw0w1PEGIHrE-kDu17u0p1wv91M0UI8v_ltKd-6gY7ZbxMqKI4oCfwU3j3soOOcf3uN4UKR1gnnMPKMZGhp4Gewl4U9TplLntw1TUgDrMQGuYwX4PYw37KUlqL-1vTl48N/?imgmax=800)
![clip_image022[4] clip_image022[4]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjv3cuih_gxcoV5k5aQ8wD5jch2sz1jxiFk2tbEERnfHojgrUzM3kyxt7hiVNQzOEegz8FJ09HDWzXzUEFAa84hGo4CWrchmEO4SIrYKu9wDIYgV1ESUmbL6Lg7g37ulualK_LYdsGe6ChS/?imgmax=800)